Topics to cover and questions to reflect on:
- What is your level of compliance with NIS2?
- What are the consequences for your business and organization for non-compliance with NIS2?
- What tools and resources are available to support making steps towards compliance?
Introduction
With the advancements in technology and the number of cyberattacks increasing, there has been a need to strengthen cybersecurity. In 2016 the NIS1 (Network and Information Systems) Directive entered into force in the European Union (EU).
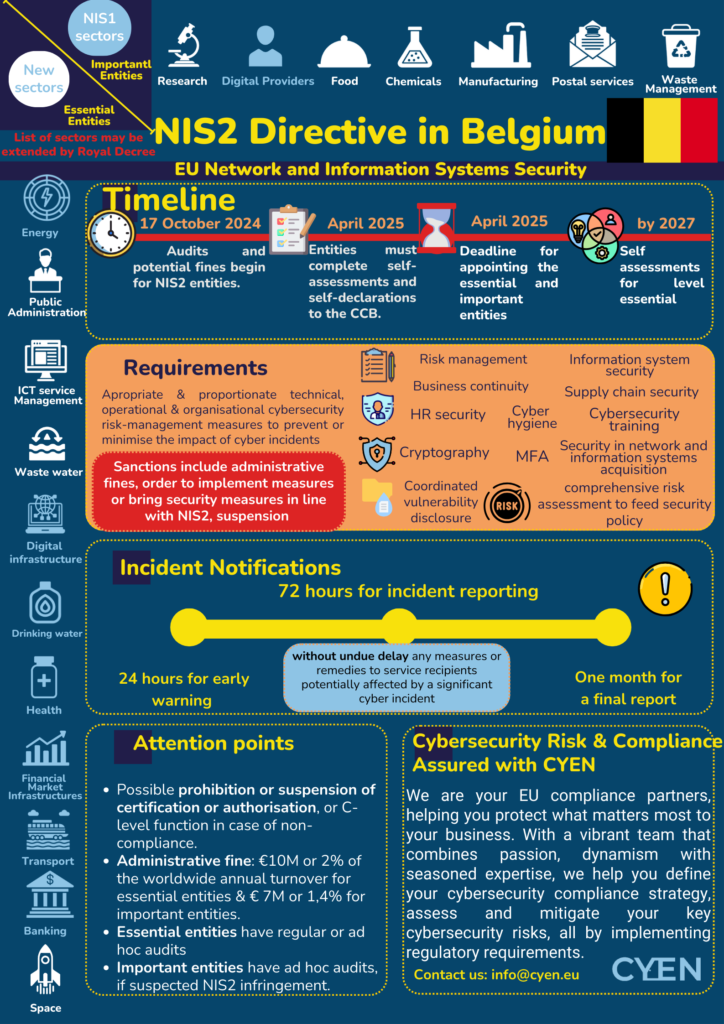
NIS2 is the revised version of the Directive, transposed into the Belgian national law and effective on 17 October 2024. The Center for Cyber Security Belgium (CCB) has been given the task to lead the process. The NIS2 law was published on the 17th of May in the Belgian Official Journal in French and in Dutch.
NIS2 is applicable to many more entities compared to NIS1. The Belgian transposition law sets the requirements for Belgian entities.
Major emphasis is on adopting a risk-based approach for cybersecurity, as well as cybersecurity measures implementation, incident management, training. Reporting significant security incidents to the competent national authorities will be mandatory. In the case of Belgium, it will be to the CCB.
In addition to the rules defined in the EU NIS2 Directive (see our infographic for reference), the Belgian law allows for additional sectors identification as essential or important, provides and encourages a CyberFundamentals certification as a presumption of conformity (as an alternative to a Government audit).
CyberFundamentals
In March of 2023, after NIS 2 Directive entered into force in January same year (replacing the 2016 directive), the CyberFundamentals Framework created by the Center for Cyber Security Belgium (CCB) aimed to advance cyber security in all Belgian companies within the public and private sector.
Cyber Fundamentals Framework that is equivalent to the ISO 27001:2022 framework on to demonstrate compliance. It is also based on NIST CyberSecurity Framework (CSF), ISO 27001 / ISO 27002, Center for Internet Security (CIS) Controls and IEC 62443. All these frameworks aim to enhance cybersecurity effectiveness and resilience, but Cyber Fundamentals Framework goes beyond ISO 27001 when it comes to requirements and guidance.It therefore aims to set concrete measures to: protect data, significantly reduce the risk of the most common cyber-attacks and to increase an organization’s cyber resilience.
The CCB´s CyberFundamentals Framework can act as a baseline of measures to help build up compliance towards NIS2 requirements.
Next important deadlines
- 17 October 2024 starts the countdown to the audit for essential entities, and the possibility for audits or fines for all entities in the NIS2 scope.
- Between 17 October 2024 and April 2025, entities falling under scope are expected to have their self-assessment considering the state of compliance and self-declaration to the CCB done.
- April 2025 – deadline for appointing the essential and important entities.
Measures and policies involved
NIS2 imposes on important and essential entities to report significant incidents within string deadlines and procedures.
- An early warning within 24 hours of becoming aware of the significant incident, which should indicate whether the incident is suspected of being caused by unlawful or malicious acts or could have a cross-border impact.
- An incident notification 72 hours of becoming aware of the significant incident, which provides an update to the early warning and an initial assessment of the incident.
- A final report within one month after submitting the incident notification, which sets out (i) a detailed description of the incident, including its severity and impact, (ii) the type of threat or root cause that is likely to have triggered the incident, (iii) applied and ongoing mitigation measures and (iv) where applicable, the cross-border impact of the incident.
The NIS2 (Article 21) specifies relevant cybersecurity risk-management measures, mentioning:
- Risk management
For risk analysis, identify the risks to system security and determine the probability of occurrence, the resulting impact, and the safeguards that are available or planned to mitigate the negative impact or probability of the risk.
- Information system security
To enhance information system security, have a strategy that includes policies to protect confidentiality, integrity and availability of information and information systems.
- Incident handling
For incident handling, improve your incident handling process by reporting significant incidents according to the NIS2 requirements.
- Crisis management and business continuity
A crisis communication plan preparing business better for unexpected events is essential. Considering business continuity, have a plan on how to ensure business continuity in the case of major cyber incidents, for example focusing on backup management and disaster recovery.
- Supply chain security
In order to enhance supply chain security, make sure that suppliers and service providers have been working towards compliance with NIS2 requirements.
- Security in network
To improve security in the network, protect your hardware and software by implementing protections such as having a Firewall, virus and antivirus software, VPN for remote access etc.
- Assessing the effectiveness of cybersecurity risk-management measures
In order to assess the effectiveness of cybersecurity risk-management measures, by setting carefully chosen metrics and KPIs that may include aspects such as number of assets, number of known vulnerabilities, vendor risk exposure etc.
- Basic cyber hygiene practices and cybersecurity training
To maintain resilience against emerging security threats, implement good cyber hygiene practices and conduct cybersecurity training to raise awareness about relevant topics in your sector and specific to your company.
- Cryptography and encryption
Have policies and procedures in place regarding the use of cryptography for secure communication and encryption, so that only authorized parties can access information.
- Human resources security
Implement a continuous employee awareness and training programme, including management messages, scenario-based training, regularly test the level of awareness (e.g. through phishing campaigns or clean desk check) and plan improvements.
- Multi-factor authentication and/or continuous authentication solutions
In order to prevent unauthorized users having access to systems and prevent falling for scams through social engineering, make sure to have secure communication lines for video, voice, text communication.
Policies
NIS2 covers different cybersecurity policies. We at CYEN recommend to also use the policy templates [13] provided by The Center for Cybersecurity Belgium (CCB) in order to create or review the following company policy documents:
- Cybersecurity policy
In order to avoid possible fines, legal fees, settlements, loss of public trust, and brand degradation, an updated cybersecurity policy taking into consideration the latest trends in the threat landscape is an important step in security.
- Access management policy
Have robust policies on access control management. Determining who has access to certain data, applications and other digital assets, and under what circumstances helps to avoid compromising situations.
- Authentication / Strong MFA & passwords policy
Strong Multi-Factor Authentication effectively blocks the vast majority of the ‘popular’ (social engineering) attacks. Passwords are essential in authenticating users. A proper password policy as a set of rules can enhance computer security significantly.
- Network security policy
By having rules on network access and implementing effective network security measures, it is possible to prevent cybercriminals from mapping the company infrastructure, disrupting communications and unlawfully gathering data.
- Vulnerability and patch management policy
A vulnerability, that is exploited by an attacker, can lead to violations on integrity, authenticity, confidentiality or availability of a system or to damage a system. With the possible consequences in mind, it is important to have a policy on how to manage vulnerabilities.
- Backup and restore policy
In case of data loss or physical damage of hardware, as a last line of defense, the backup and recovery policy plays a critical role in ensuring data security and regulatory compliance.
In addition to the NIS2 measures, Belgian transposition law includes additional risk management and information obligations:
- coordinated vulnerability disclosure policy
- conduct a comprehensive risk analysis that considers all potential risks, in order to safeguard networks, information systems, and physical environments against incidents, serving as a basis for a security policy.
The list of obligations can be further extended by royal decree.
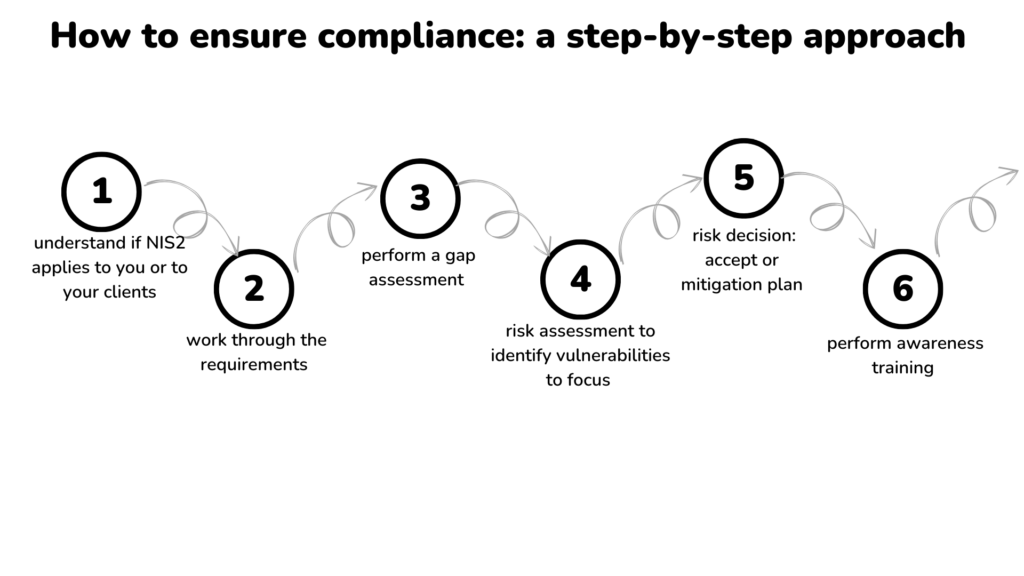
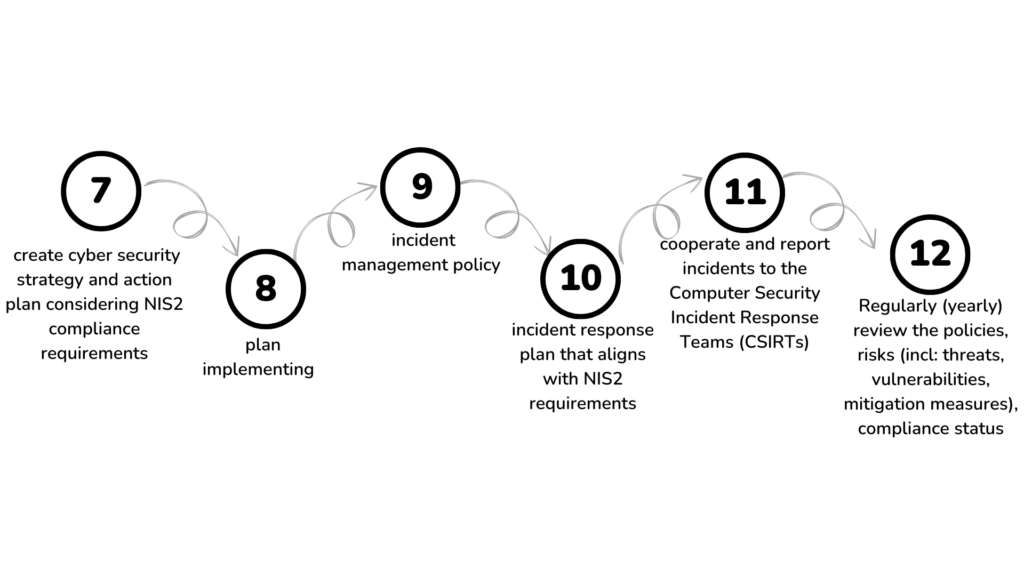
More advice is available on Cyen’s YouTube channel. Cyen has extensive experience and provides cybersecurity awareness, governance, risk and compliance management, and third-party security services. Contact us at info@cyen.eu or book a free meeting with one of our experts here to discuss further or if you need help.
Other support and resources available
- Follow the updates on the topic by The Centre for Cybersecurity Belgium (CCB) which is the national authority for cybersecurity in Belgium.
- The Cyber Security Coalition has created a Cyber Security KIT for SMEs and organizations to raise awareness about cyber security among their employees that is available in English, French and Dutch.
- The Centre for Cybersecurity Belgium (CCB) has produced a set of customizable and editable cybersecurity policy documents that may be adapted according to the needs of the company or organization.
- The Global Cyber Alliance (GCA) Cybersecurity Toolkit for Small Business that helps to reduce cyber risk.
- The Interdependencies tool contributes to the NIS Directive (Article 3), as the web tool presents the mapping of indicators to the corresponding information security standards/frameworks (ISO, NIST, COBIT5) in an easy-to-use web-based format.
- The Mapping of Security Measures for OES Tool contributes to the NIS Directive (Article 3), as it provides the mapping of security measures for OESs to international standards used by operators in the business sectors (namely energy, transport, banking, financial market infrastructures, health, drinking water supply & distribution and digital infrastructures).
- So-Cyber is a partner company that can help with penetration testing, vulnerability assessment and management.
- Cyen, focused on cybersecurity risk and compliance consulting, can help with conducting research and creating a cybersecurity strategy.
- ENISA AR-in-the box tool for setting and improving cybersecurity awareness programme.

Recent Comments