In this article we will look into the cybersecurity requirements of the GDPR and will point the attention of companies to the immense amount of possibilities for data breaches there are. We will discuss the lessons learnt from previous large-scale data breaches and will put forward recommendations for companies on how to tackle the challenging threat landscape and what cybersecurity measures they can take to better protect the personal data they handle.
GDPR: 5 years on
On the 25th of May 2023 the EU celebrated five years since the entering into force of the GDPR, the General Data Protection Regulation. A landmark piece of legislation, it has become an example of data protection legislation and many states outside of the EU have adopted similar laws (e.g. the UK GDPR, Japan’s Act on the Protection of Personal Information (APPI), reviewed in 2016, Brazil’s Lei Geral de Proteçao de Dados (LGPD) 2018, Switzerland’s Data Protection Act “Datenschutzgesetz” (DSG) 2020 etc.).
Enforcement review
In 2023 the European Commission announced that the GDPR is to be reviewed so that it would streamline the cooperation between the national Data Protection Authorities in cross-border cases related to enforcing the GDPR. By 25th of May 2024, the 6th birthday of the GDPR, its first major review should be published. This would coincide with the elections for the European Parliament, therefore the negotiations on the review and subsequent implementation and enforcement deadlines may be delayed until the new legislature settles in.
Securing the personal data
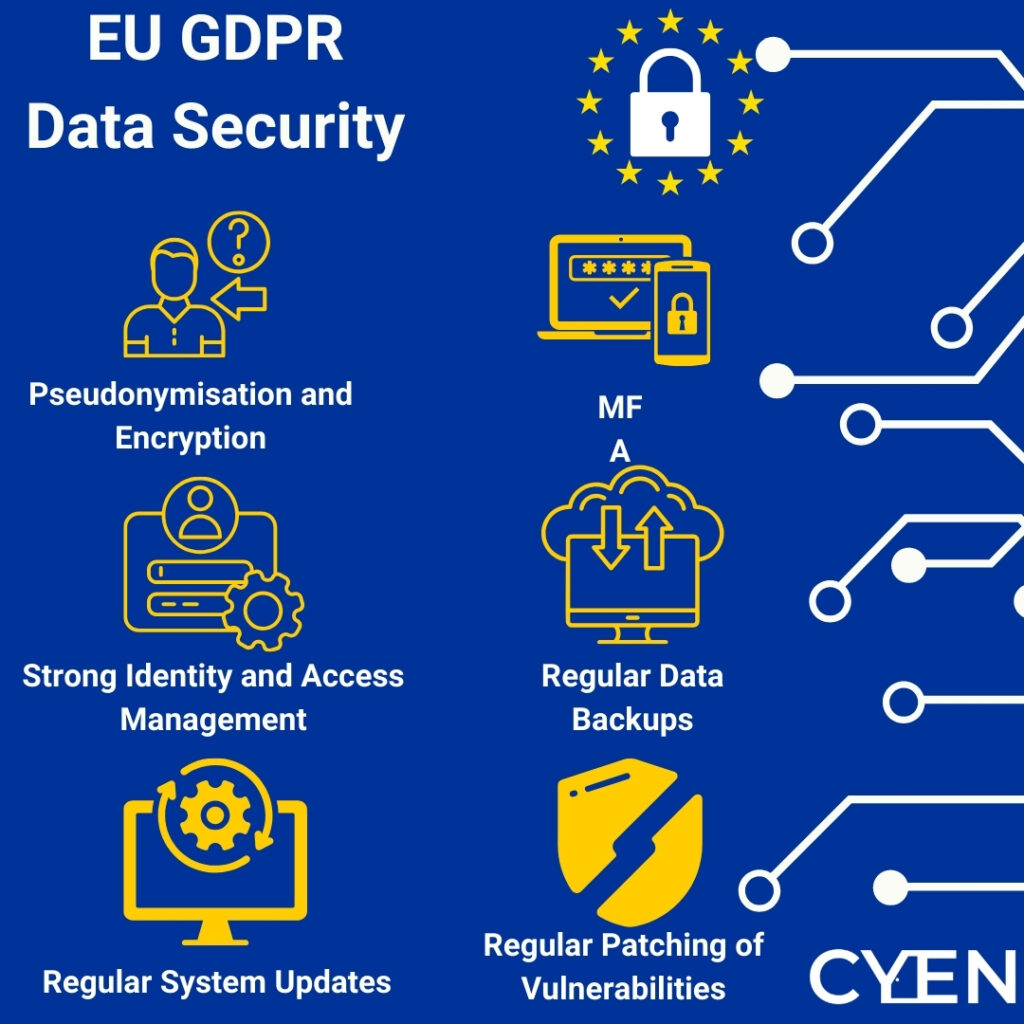
All companies need to be able to ensure the ongoing confidentiality, integrity, availability, and resilience of processing systems and services; need to be able to restore the availability and access to the personal data in case of a security incident; and they also need to regularly test, assess in evaluate the effectiveness of the technical and organisational measures that ensure the security of processing. A list of what some of these technical and organisational measures entail has been also provided by the GDPR. Such measures are, for instance, pseudonymisation and encryption of the personal data; multi-factor authentication, strong identity and access management, regular data backups, regular system updates, regular patching of discovered vulnerabilities. For the more mature companies and those handling huge amounts of personal data such as public administrations, for instance, the resilience of the processing systems and services should be regularly tested using, for example, penetration testing. Regular employee training is also key to successfully enforcing the GDPR as human error is one of the most common reasons for data breaches (ENISA and the EDPS conference 2019). DPAs and EU institutions (EDPB/EDPS) developed a number of guidance documents on many specific topics addressed in the GDPR – for instance on automated decision making, secure data erasure, pseudonymisation – providing details and clarifying what the requirements are specific.
Any company handling personal data, therefore, would have to adopt the measures put forward in the GDPR: from the smallest startup processing the data of only one client, to the public administrations handling all of the personal data of the citizens in a given region/state/etc.
A company can be in violation of the articles regulating security regardless of the cause: a breach and – as a consequence a personal data leak – can be accidental or deliberate, it can be due to malicious third party trying to access sensitive company data, it can be a foreign state performing a cyber espionage operation, it can be data leaked by an employee. In the eyes of the national Data Protection Authority, however, the cause is of little importance (clearly decided on a case-by-case scenario), because the GDPR’s Article 32 Security of processing, requires companies to adopt some technical and organisational measures for the protection of the personal data they collect.
But the technical and organisational measures would differ from company to company – each company needs to take those measures that are proportionate to the risk it is exposed to. This means that each company needs to have a well-defined cybersecurity risk management policy that identifies the risks, the threats and the appropriate measures to be taken to protect the sensitive data. A company operating in the software business and a company operating in the carpentry business, for instance, would clearly have different security risk management policies and as a consequence would have to adopt different technical and organisational measures to protect the personal data of their clients/customers/users.
Failing to implement the appropriate technical or organisational security measures the GDPR prescribes fines up to €10 million or up to 2% of the total annual worldwide turnover for the preceding financial year, whichever is greater.
GDPR as part of the EU cybersecurity regulatory puzzle
Companies need to remember that all GDPR incidents are security incidents – but not all incidents are GDPR incidents. Which means that in terms of regulatory measures, there is always the possibility of a major data leak that violates not only the GDPR. For instance, if there were an attack against a hospital, handling large quantities of patient personal data, and if that hospital were identified as an ‘essential’ entity under NIS2 Directive, the breach would make it liable under both the GDPR and the NIS2 Directive. (The NIS2 Directive regulates security measures and incident notification for ‘essential’ and ‘important’ entities operating in the critical infrastructure sectors such as health, transport, energy, finance, manufacturing, etc. For more detailed analysis on NIS2 and what it means for SMEs, read our blog post here). The hospital would hence be liable under the GDPR for not having adopted the necessary – proportionate to the risk! – technical and organisational security measures to secure the data, and under the NIS2 Directive for not having taken the necessary appropriate and proportionate technical, operational and organisational measures to manage the risks posed to their security of network and information systems. Because we talk about personal data breach – clearly the GDPR violation would “prevail”. However, the fact that the company in question is an essential service under the NIS2 Directive could be considered as an aggravating circumstance.
After having become aware of the incident, both the GDPR and the NIS2 Directive have set a timeframe for incident notification. According to the GDPR’s Article 33, companies need to notify a data breach within 72 hours to the competent national supervisory authority. According to Article 23 4. (b) of the NIS2 Directive, the same 72 hours were imposed to essential and important entities to notify their national CSIRT or competent authority. This alignment of security laws was a welcomed step as it streamlined the whole process and created less burdensome requirements for companies, wondering which law they should first adhere to.
The role of the third parties in processing personal data
It is also important to mention that the GDPR differentiates between a ‘controller’ and a ‘processor’ of personal data. ‘Processors’ are companies which process personal data on behalf of the controller. Processors are hence third parties and as such it is always good to keep in mind that in the last few years there has been a rise in attacks on third parties, the so-called supply chain attacks. In fact, in our Predictions for Cybersecurity in 2023blog, supply chain attacks were listed as one of those cyber threats to see a continuous rise in 2023.
According to Article 28 GDPR a company acting as a ‘controller’ of personal data is liable for both its own compliance with the GDPR, and the compliance of its ‘processors’. This means that if the processor has failed to implement the technical and organisational measures for protecting the personal data, and has suffered a data breach, the controller could also be held responsible and could be subject to fines. This is because the controller and the processor have signed a binding contractual arrangement under Article 28 3. and in line with these contractual arrangements, the processor has agreed to take all the measures in Article 32 listed above to secure the personal data. This means the processor would be liable for its own compliance with the GDPR, but would also be liable to the controller for breaching the contractual arrangement.
Major security incidents under the GDPR
There have been some major incidents across various member states:
– In January 2021 the French Data Protection Authority (CNIL) fined a controller for inadequate measures to deal with credential stuffing attacks. CNIL considered that the data controller and processor had been slow in creating a tool for detecting and blocking cyber attacks, as well as noted that they had failed to take measures, such as using CAPTCHA for user account authentication or limiting the number of requests per IP address. In addition, in deciding the fine, CNIL noted the data controller’s obligations to implement technical and organisational security measures and to give documented instructions to its processor.
– In 2018 British Airway was fined £20 million(the initial penalty was £183.39 million!) because due to poor security management it had allowed a data breach related to the personal data of approximately 429,612 of its users. Data such as names, addresses and bank card details were leaked. The Information Commissionser’s Office stated that it “has found that BA failed to process the personal data of its customers in a manner that ensured appropriate security of the data, including: protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical and organisational measures, as required by Article 5(1)(f) and by Article 32 GDPR.”
– In 2019, the Bulgarian National Revenue Agency was targeted by a malicious attackand its security systems were breached. The personal data of over 5 million Bulgarian citizens was downloaded and some of it was leaked to the public. The national revenue agency was fined with around €2.5 million for not having sufficient security measures in place.
– In 2021 the Dutch Data Protection Authority issued a fine of €440,000 to OLVG, a hospital in Amsterdam, because it had failed to protect patients’ medical records. Between 2018 and 2020 OLVG had not taken the necessary technical and organisational measures to prevent unauthorised access to the personal data.
These examples have evidenced that even after that many years (the GDPR was officially adopted in 2016!), some personal data controllers and processors have still not taken the necessary technical and organisational measures to properly secure the data they handle.
Lessons learnt and recommendations
The GDPR has been in force for five years now and companies no longer have the excuse of not being aware of the security measures put forward into it.
As mentioned, human error is one of the most common reasons for data breaches, as are hacking, for instance using malware or phishing (ENISA & EDPS Conference 2019). This means that at the bottom of every data breach there is either an outdated system, outdated equipment or untrained employee. Companies do need to invest in cybersecurity awareness training, they do need to adopt the necessary cybersecurity measures such as multi-factor authentication, strong identity and access management, regular data backups, regular system updates, regular patching of discovered vulnerabilities, because a data breach means economic losses, lost customer/user trust, reputational damage and, potentially, in terms of long-term impact – going out of business.
We at Cyen provide companies with the latest cybersecurity intelligence, we hold workshops on various topics such as third party risk management, basic cybersecurity awareness, and we support compliance with EU cybersecurity legislation and information security standards (ISO27k, PCI-DSS). We also hold tailor-made employee trainings and provide various levels of security assessments for companies and their third parties.
EU GDPR DATA SECURITY

Recent Comments